PacketSafari PCAP Sanitization

Officially Endorsed
Wireshark Foundation
The Wireshark Certified Analyst (WCA) Complete Course
Official Wireshark Certified Analyst - The Complete Course
Backed by the Wireshark Foundation, this immersive program shows you exactly how to troubleshoot, analyze, and secure packet flows with confidence.
- Hands-on Wireshark labs that mirror real packet captures.
- Master Ethernet, ARP, IPv4/6, TCP, ICMP, and more.
- Follow a guided progression that keeps you focused and confident.
PacketSafari partners with top training providers—purchases through this link help us keep building free labs and articles.
PacketSafari is proud to announce our most requested feature: in-memory PCAP sanitization. This process involves stripping away sensitive or unnecessary data from PCAP files while retaining only the essential header information.
Why Sanitize PCAPs?
- Protecting Sensitive Data: PCAPs can capture far more than just network headers; they often include application payloads, personal data, or proprietary information. Sanitizing these files ensures that only the essential header information is retained, significantly reducing the risk of exposing sensitive data.
- Enhancing Data Security: By removing unnecessary details, the sanitization process minimizes the risk of data leaks and aids in complying with privacy regulations. This is particularly crucial in multi-tenant SaaS environments where protecting customer data is of utmost importance.
Our implementation
In this release, we introduce slicing mode as the primary sanitization approach. You can now choose to sanitize files upon upload, ensuring your data is protected from the start. Slicing mode is designed to be the safest option to remove data by ensuring that only packet information up to a certain offset is retained. For users who also wish to anonymize IP, Ethernet, and other headers while still prioritizing privacy, we offer the deep anonymization option.
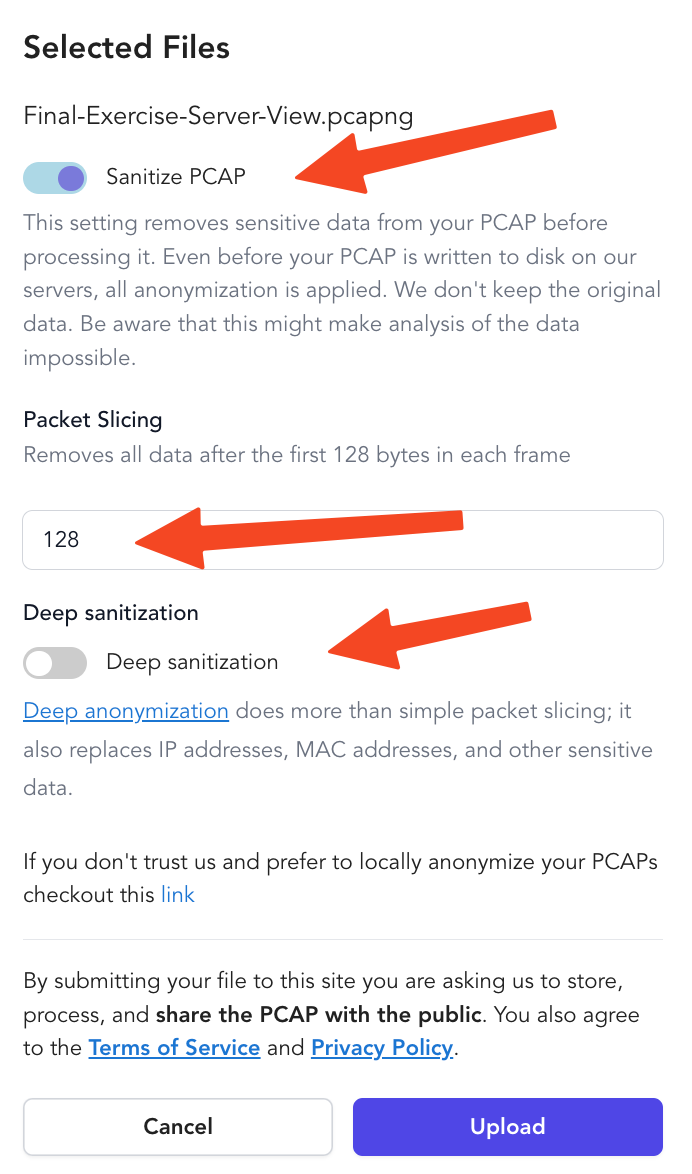
Upload your PCAPs here
Slicing Mode: The Safest Approach for Data Privacy
In slicing mode, PacketSafari truncates each packet to a defined snaplen—the maximum number of bytes preserved from each packet. This method ensures that only the essential header information is retained, completely excluding any potentially sensitive payload data. By doing so, we minimize the risk of exposing application-level data, making it the most secure approach when data privacy is a paramount concern.
Key Features of Slicing Mode
- Data Removal: Only the first few bytes (typically containing header information) are preserved, ensuring that sensitive data is never stored or processed.
- Fast and Efficient: The algorithm simply truncates the packets without the overhead of deep field-level modifications.
- Ideal for High-Security Environments: Perfect for scenarios where absolute data sanitization is required to prevent any sensitive information leakage.
Deep Anonymization
Although slicing mode ensures maximum safety by removing nearly all payload data, there are situations where you may need to anonymize additional details such as MAC addresses and IP addresses. For these cases, PacketSafari offers the deep anonymization option.
How Deep Anonymization Works
In deep mode, the sanitization algorithm processes each packet in detail to anonymize specific fields while recalculating checksums to maintain protocol integrity. This approach retains more of the packet's structure, which can be crucial for analysis by advanced tools or LLMs (Large Language Models). The following protocols and fields are processed:
- Ethernet Layer:
- MAC Addresses: Both source and destination addresses are anonymized using a hash-based mapping while preserving broadcast and multicast addresses.
- IPv4 and IPv6 Layers:
- IP Addresses: Sensitive addresses are modified (except for special cases such as loopback, multicast, or broadcast addresses). Recalculation of checksums ensures packet validity.
- ARP, ICMP/ICMPv6, DNS, DHCP/BOOTP, DHCPv6, and RIP:
- Protocol-Specific Fields: Each of these protocols has key fields that are sanitized, such as anonymizing ARP hardware addresses or modifying ICMP IDs and sequence numbers.
Both modes can be used together. Slicing is always active by default; however, if you set the snap length to a high value, slicing is effectively bypassed.
Why In-Memory Sanitization?
Both the slicing and deep anonymization modes operate entirely in memory. This design ensures that sensitive data is never written to disk, thereby reducing the risk of data exposure. By processing PCAP files solely in memory, PacketSafari maintains a high standard of security during file uploads and analysis.
Additional Resources
For users who prefer to sanitize PCAP files on their own system, we recommend reviewing our detailed guide on manual anonymization. This guide explains various tools and techniques you can use offline if you do not fully trust our algorithm:
PacketSafari continues to evolve based on your feedback. Whether you choose the highly secure slicing mode to protect application layer data or opt for the more detailed deep anonymization for comprehensive analysis, our new sanitization features are designed to meet your security and analytical needs without compromise.

