Solving TryHackMe Wireshark Filters room with PacketSafari - Part I Protocol Filters

Officially Endorsed
Wireshark Foundation
The Wireshark Certified Analyst (WCA) Complete Course
Official Wireshark Certified Analyst - The Complete Course
Backed by the Wireshark Foundation, this immersive program shows you exactly how to troubleshoot, analyze, and secure packet flows with confidence.
- Hands-on Wireshark labs that mirror real packet captures.
- Master Ethernet, ARP, IPv4/6, TCP, ICMP, and more.
- Follow a guided progression that keeps you focused and confident.
PacketSafari partners with top training providers—purchases through this link help us keep building free labs and articles.
Introduction
Solving the TryHackMe Wireshark Filter room with a SaaS application like PacketSafari can be very convenient. It allows you to easily and quickly analyze network traffic without installing and setting up Wireshark on your local machine. This can be especially useful if you are working on a device that doesn't have Wireshark installed or need the necessary permissions to install it. PacketSafari is also meant to be a public archive of PCAPs and analysis for educational purposes.
PacketSafari is a cloud-based application, which means you can access it from any device with an internet connection, making it very convenient to use. PacketSafari offers some advanced features and tools for analyzing and visualizing network traffic, which can make solving a Wireshark filter room more enjoyable and effective.

The first part
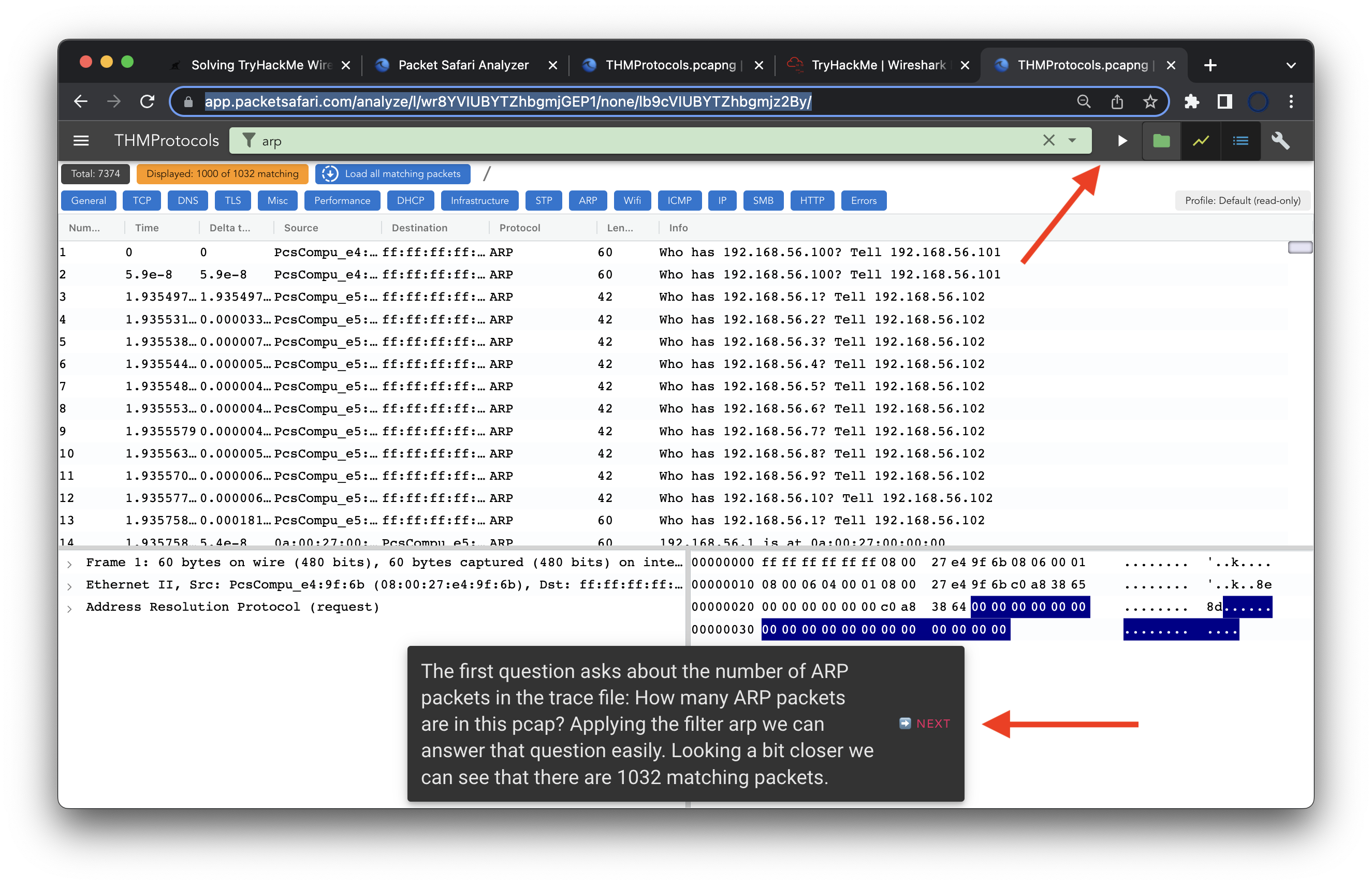
The first part of the room is about applying simple protocol filters. Let's try to solve it using PacketSafari. You can open the PCAP directly in your browser using PacketSafari. Click here to see the data.
The first question asks about the number of ARP packets in the trace file: How many ARP packets are in this pcap?. Applying the filter arp we can answer that question easily.
ARP Filter
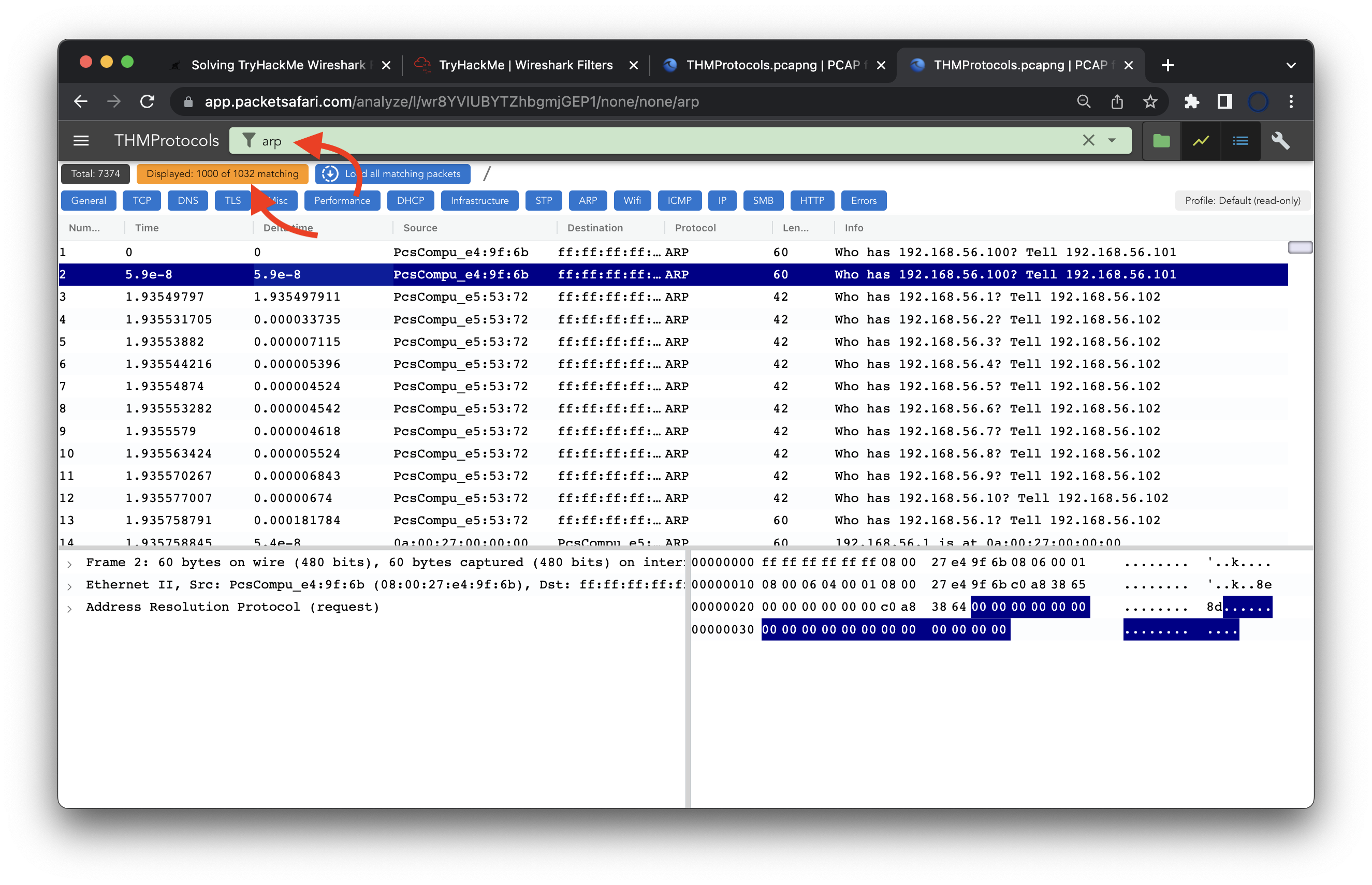
Looking a bit closer we can see that there are 1032 matching packets. PacketSafari currently displays only 1000 of these packets. This is an optimization for the application to be more responsive. You can of course load all matching packets by clicking on Load all matching packets. If you have a PacketSafari account you can also change the default limit of 1000 to a higher value.
One cool feature of PacketSafari is the possibility to link directly to a filtered PCAP. The following link directly solves the first question: solution to first question
Solving the other questions
The second question we can solve similarly by applying the filter ip with a matching 6342 packets.
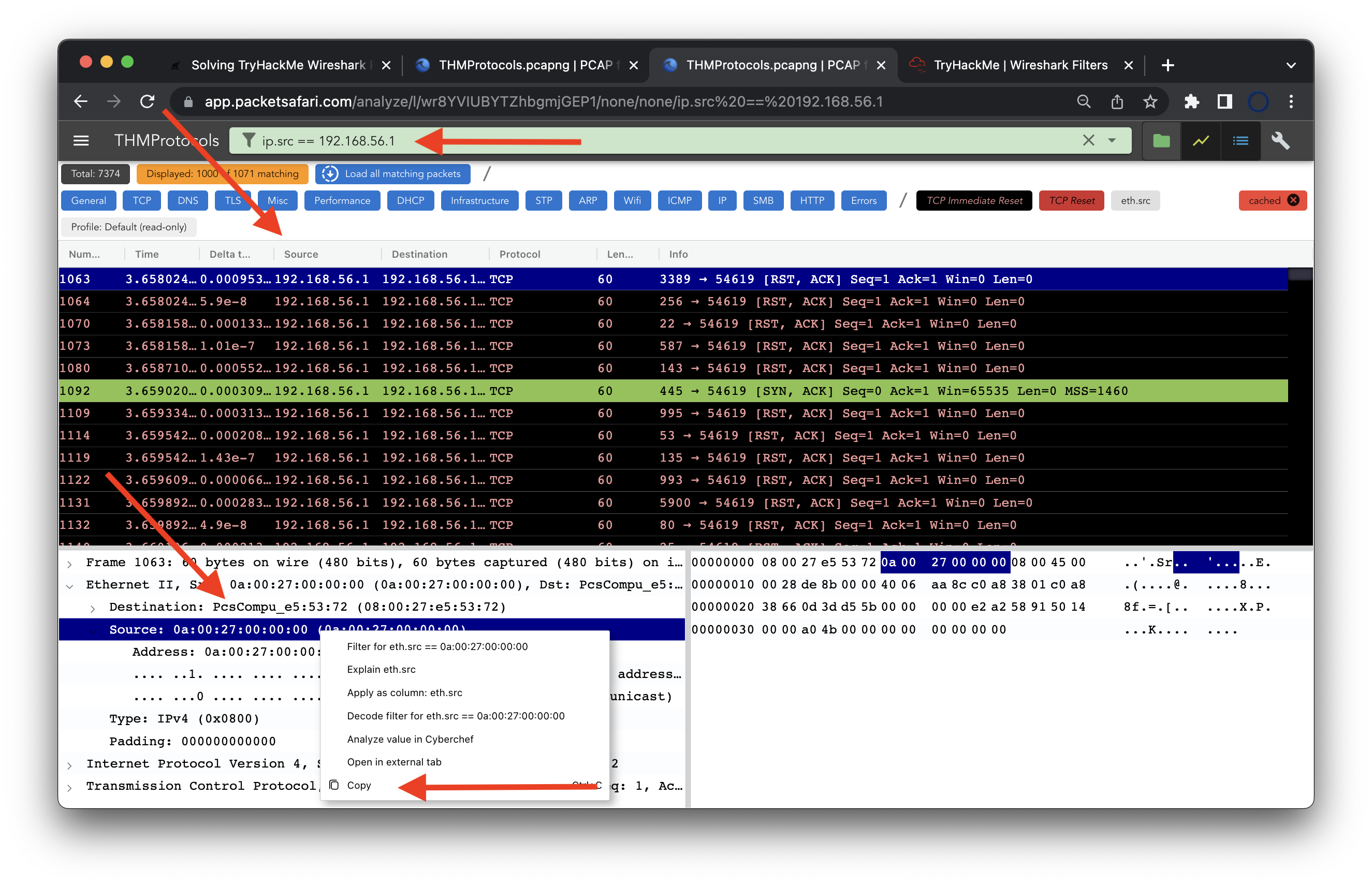
Now, the third question is a bit more interesting as we need to filter first and then look at the packet details in the lower left part of the screen. First, we filter for the requested IP address ip.src ==192.168.56.1. In the screenshot, we can see the applied filter. The source column shows the correct IP address. Finally, at the bottom, we can find the source mac address and copy it using right-click -> copy.
The number of ICMP packets is again very straightforward icmp with a total of 1064 packets. And the non-ICMP packets not icmp with a total of 6310 packets and TCP packets tcp with 6293.
A more interesting filter again is TCP packets that are not encapsulated in ICMP. As you might now ICMP can quote certain packets which happens quite often with destination unreachable packets. Using the filter tcp and not icmp we can answer with the correct number of 5269. It works similar for udp: udp and not icmp. Here we are left with only 9 packets.
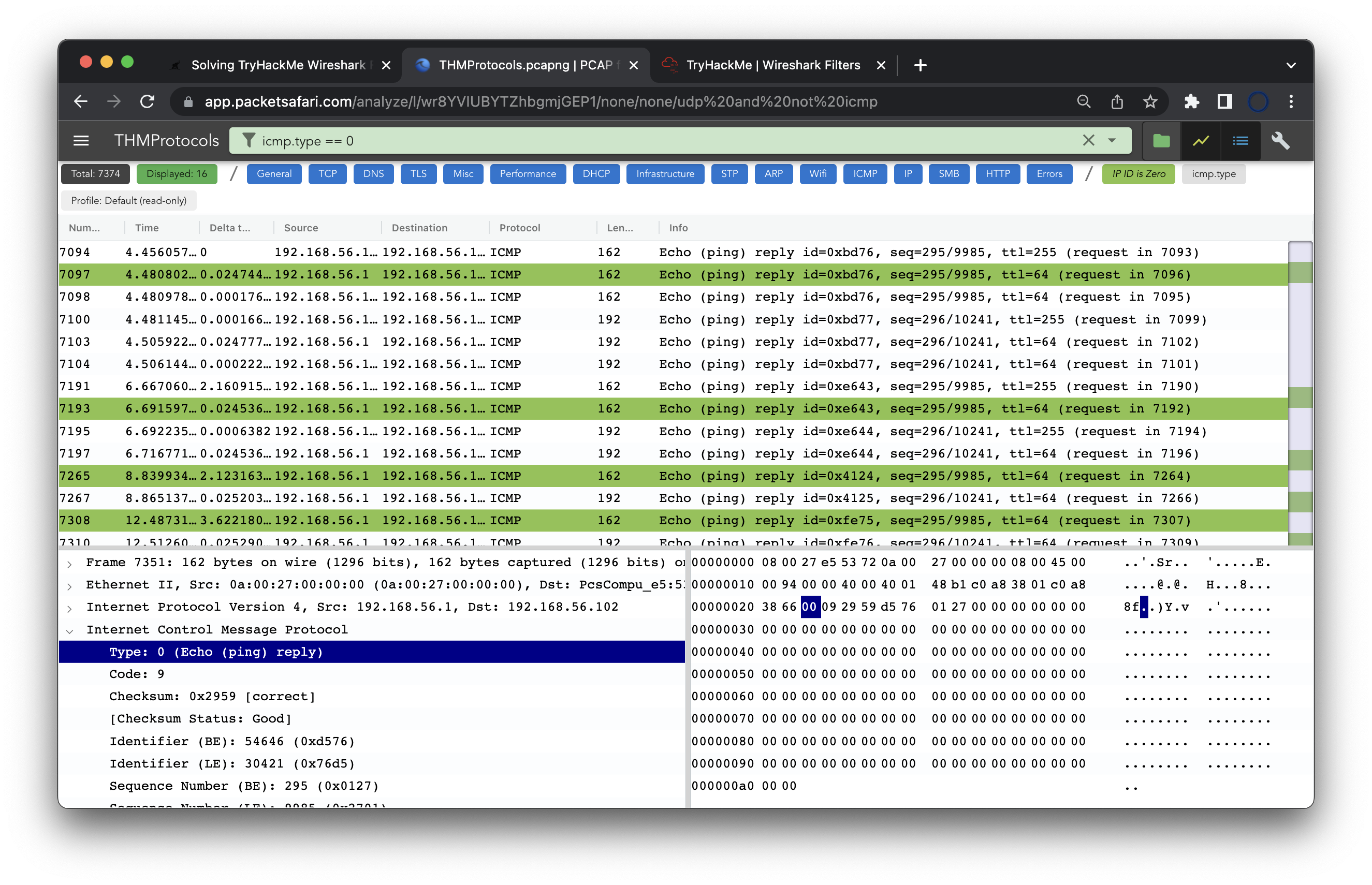
The last question is about ICMP Echo replies. These packets have a type of 0. So this filter will do fine icmp.type == 0, ending up with 16 packets.
PacketSafari analysis recording
One cool feature of PacketSafari is to document your analysis right within the PacketSafari app. Click on this link to open the interactive analysis.
Click on next in the bottom overlay or the play button in the navigation bar to go to the next solution.
That's it for now. This was the first part of our series about this packet analysis room. You can also find a walkthrough video from Chris himself on Youtube.

